Privacy on the Internet is… well, let's just say it's complicated. In this article, I'll analyze a few open source tools and concepts that you might use to increase privacy on the Internet for yourself. It will not be an exhaustive list of all possible avenues, nor does it pretend to ensure complete privacy even in the face of a concentrated, personal attack. Some of the tips you will find useful, others you will discard, and still others you might use in conjunction with other policies to construct your own privacy model.
The concept of privacy is a difficult thing to pin down. It gets muddled up with other big ideas, like anonymity and secrecy and even criminal activity. Whatever "privacy" means to you and whatever you might associate it with, most people agree that we have a right to it, if not necessarily online or in public, then at least on some level.
That means that some portion of our computing life should also have the privilege of being private. How far that extends differs from one person to another. For one person, an implied guarantee of privacy is sufficient (a website wouldn't require a password if it didn't intend to keep user data private, right?), whereas another might prefer to use aliases for online interactions and nameless spending accounts that cannot be traced back to the real world.
Another thing that differs from one person to another is the price they are willing to personally "pay" for privacy. It's a balancing act, after all. Is "mostly" private good enough for you? Or are you willing to invest more time and effort into ensuring that your information and information about you is concealed no matter what?
The basics
Let's start with the basics, because they bear reinforcement. Much of the confusion about online privacy can be summed up with this simple adage, which adorns many an open source geek's laptop in the form of recent FSFE stickers:
There is no cloud, only someone else's computer.
Your computer privacy stops at your modem. Some people are OK with this, others are not as comfortable with the idea. When you do something online, online shopping, for example, there is no guarantee of privacy because you are logging onto someone else's computer. There is usually the implication that what you do on their computer will stay between you and them, but it's out of your control and sometimes even out of their control.
Keep that in mind going forward, because that's what privacy concerns always boil down to. Your online privacy is only as strong as the weakest link in the chain consisting of you, your ISP, and the places you visit on the Internet.
A long-standing tradition of network communication, electronic mail can theoretically be achieved in a direct computer-to-computer action. In today's inter-networked world, however, you can rest assured that any email message you send over the Internet touches down on at least one third-party system before reaching its final destination. There's SSL to make this process "secure," and there are varying levels of agreements and "guarantees" that your emails will only be opened by their intended recipient.
If you're fine with that, then continue as usual.
If you're fine with it, but would prefer a layer of obfuscation, then you can encrypt your email so that only the intended recipient can decrypt it.
Encrypted email
To encrypt an email message, you need to get started with gnuPG (GPG, an implementation of PGP). Many people, even some ardent proponents of GPG, critique it for being difficult to learn and to use, but in reality it's a lot like backing up: We all know we should do it, and it's not something that's technically complex, it's just a matter of getting everyone to actually do it that seems to be the hurdle. Sure, it might be nice if email clients (both desktop and web-based) insisted upon some encryption backend to leverage, but for now it's a voluntary system that requires users to take a few brave steps of their own into the world of key-pair encryption.
To get started with GPG, create a GPG key. Follow the instructions to generate a new key for yourself. Using the defaults for each question is fine, but do provide a password when asked.
In the end, you'll receive a notice about a new GPG key. For example:
gpg: checking the trustdb pub 2048R/934EFCA4 2015-12-27 Key fingerprint = 1A5A 46FD F7D8 3509 8B26 049C 1C8E C11E 934E FCA4 uid Alan Smithee (This is a fake key, generated as a demonstration.)sub 2048R/D62BB11D 2015-12-27
Now that you have a GPG key, post your public key on the Internet, preferably on a PGP Keyserver. First, find your public key ID. The 2048R/ after pub in the example above refers to the type of key it is (2048 bits), and the number following it is the key ID. So in this example, the key ID is 934EFCA4.
Send this key, using its ID, to a keyserver so that other people can find and use it. That probably seems counter-intuitive in an article about privacy, but privacy isn't necessarily the same as anonymity. Of course, there's nothing saying you can't use an assumed name for your encryption key, but a public key is only useful to other people as an encryption tool. It's something you want other people to have.
This is how encrypted email works: If someone wants to encrypt a message and send it to you, they can use your public key to do that, and since your computer now has a private key that matches the public key that you posted for the Internet to discover, you (and only you) are able to decrypt the message and read it. So post your public key online so that your friends can start encrypting messages to you. And then go get their keys so you can encrypt messages meant for them.
Thunderbird, Evolution, KMail, Claws Mail (with PGP plugins enabled), Rmail (with the epa module), Mutt, and most other open source email clients make encryption and decryption with PGP almost transparent to the user. All you have to do is point your email client to your GPG key, and it will handle everything else, from encrypting outgoing messages to decrypting incoming ones.
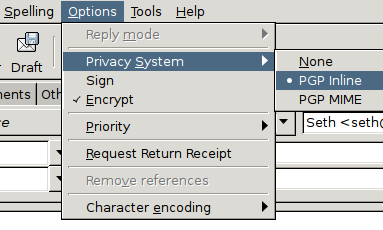
The catch is that in order for the system to be useful, your contacts must also use it. You can't encrypt messages to people who have no way of decrypting them, and you can't receive encrypted messages from people who don't encrypt.
Personal email server
When you let a third party host your email service for you, you are forcing a middleman into not just some, but all of your communication. All messages received at your email address are actually sent to someone else's computer; you are then permitted to log into that computer and retrieve your messages. It's the old Post Office model in electronic form.
Third-party hosting is not necessarily as sinister and scary as you might think I'm trying to make it out to be. The Internet is a whole network of services, so the fact that emails are shuffled from one server to another on the behalf of millions of users is par for the course. However, if you are interested in bringing services under your control rather than handing over your data to someone else voluntarily, then sending and receiving email on your own server is a great solution.
Hosting an email server has only gotten easier over the years. Unless you intend to open a new email hosting company, you can use an old "outdated" computer as your server, and there are some specialized Linux distributions, like ClearOS out there aimed at being easily configured email servers. Even setting it up manually is not really more than an afternoon project. Rather than glossing over the steps here, I'll send you to LinuxMail.info for step-by-step instructions.
There are several ways to run an email server, but with modern applications like Postfix and Dovecot, the configuration can be minimal.
Furthermore, there are several providers of no-cost domain names, and dynamic DNS. Just set your domain's mail (MX) server to your personal server, and you've cut out the most obvious and immediate third party involved. You can even take your pick from one of several open source email frontends and install your own webmail client, like Roundcube so you can access your mail from any computer through a web browser.
Your own cloud
Since the Internet offers so many useful services now, ignoring them is almost counter-productive. As with other online services, though, you are literally composing documents and spreadsheets on someone else's computer. Probably there's an agreement that your data is private, but if you want a better guarantee of that, you can set up and run your own cloud with ownCloud.
OwnCloud, for being a private SaaS, is simple to set up. As with running your own email server, you do need your own server in order to host ownCloud and maximize privacy. You can run it on most virtual private servers (VPS) or shared hosting accounts, but that introduces a third party, which is not ideal (although it does at least skirt the issue of using an instance of someone else's application).
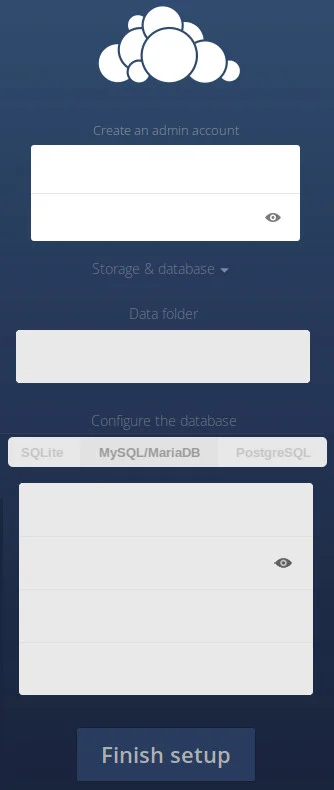
To install ownCloud, download it onto your server and un-archive it into a web-accessible directory (such as /var/www/htdocs or whatever you use as your web directory).
In a web browser, navigate to the ownCloud directory and follow the installation instructions. If you use an SQLite database, the setup is as close to automated as you could want, but if you want to enable multiple users, you'll need to use the MySQL or MariaDB as your backend (which also means you'll have to set up a MySQL or MariaSQL user and database, but the process is simple and well documented).
Once installed, ownCloud can be your online file sharing solution (like Dropbox, with local directory sync for desktops and mobile platforms), an online document-creation solution, potentially an online office suite (with a LibreOffice plugin, although this requires considerable setup and is still very much in a beta-like state), a calDAV server, and much more.
In short, with ownCloud as your personal cloud, you will find little need for online storage and office solutions outside your own server.
Identity online
At nearly every turn, the Internet invites you to provide information about yourself, your friends, your employers or employees, your whereabouts, your plans, your personal history, your hopes and dreams, and more. Probably most of this information is white noise in a sea of all the same information for a million other users, and probably most of that same information could get put online by your own friends if you weren't providing it yourself. That doesn't mean you have to settle for it, though.
If you have nothing to offer people online when they want to refer to you, then they'll naturally just refer to you as they know you in the real world. You can ask them to never mention you online, but realistically, that doesn't scale; you might get your best friend to never mention your full name online, but you can't force everyone you come into contact with to never talk about you in public.
What you can do, however, is gently re-direct them to an online identity that does represent you, while also not betraying you. In other words, give your friends and family a common persona online for them to use when they inevitably want to refer to you and tag you in photos and so on. Everything about this persona can be completely different from your real life. Your online persona can live in a different country, have a different marital status (you'll want to explain this to your real life partner first, though), have a different birth date, have a different job, and so on. The name could be your name or a misspelled version of your name, or a variation on your name, or something completely different, if you're comfortable with proudly taking ownership of an online handle. This thin layer of misdirection gives you the best of both worlds: It misinforms data-miners, while also providing your friends and family an online outlet to connect with you.
The same goes for mobile accounts, the information you enter when signing up for an account on websites, and even your online CV. Planting a few seeds of wrong information can be an invaluable privacy tool, not just to prevent others from stumbling upon important identifying data, but also for you to recognize mined data when it surfaces later on.
The Open Part of Open Source
Open source tools help you build a platform on your own terms. Open source doesn't guarantee that an application is more secure than any other, nor does it mean that your privacy is magically secured. Open source thrives on community and a web of trust; follow the development of your favourite projects, get to know their lead developers and their values, and get to know the software. Start using the software, with privacy as the main goal, and you'll see why an open community actually helps create a more respectful, private, and secure digital life.
Keep safe
Moving toward better privacy online can turn into a lifelong project—if you're paranoid enough—but that's not really the point. Instead, make online privacy a way of life—something that becomes normal for you, so that you don't need to worry about what information about you has made it out to the Internet. Take small precautions or take big precautions, but take them often, as a habit, and let privacy be a side effect of your online activity rather than a casualty of it.






1 Comment