Recently, Lee Brian wrote a great article about her own Linux story in My Dad, Linux and Me. In some of the comments to that article, a discussion of viruses and Linux emerged. While most of the Linux community would agree that viruses are less of an issue in Linux than some other operating systems, there are some people we share files with who are affected by viruses and other malware.
Maybe you have a shared folder on your computer that Microsoft Windows users access. Perhaps the IT department where you are employed requires the installation of antivirus software on all computers on your network. How do we protect them and ourselves in such environments?
That's where open source antivirus engine ClamAV comes in. I have been using ClamAV on Mac OS X and Linux for almost 10 years and find it to be an effective deterrent to trojans, viruses, and malware. Its source code is available on GitHub under the GNU Public License.
On Linux servers, ClamAV can be run as a daemon. It can service requests to scan files sent from other processes. These can include spam filters or files on Samba shares. ClamAV typically runs from the command line, but there are third party developers who have created graphical user interfaces for it.
On Fedora:
dnf -y install clamav clamav-update
On Ubuntu:
sudo apt-get install clamav
For other versions of Linux and Unix, instructions are available.
Once ClamAV is installed, updates can be obtained by switching to root with "su" or "sudo" and entering "freshclam" on the command line. After updating the virus definitions, you're ready to scan your system. There are many options that can be used when scanning, and you can refer to this man page for options.
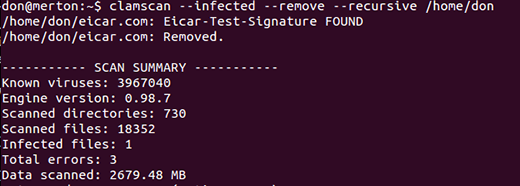
My own favorite is clamscan --infected --remove --recursive /home, which recursively scans my home directory and prints out the infected file.
Equally important to maintaining the integrity of your system is the detection of rootkits. According to Wikipedia, "A rootkit is a collection of computer software, typically malicious, designed to enable access to a computer that would not otherwise be allowed (for example, to an unauthorized user) while at the same time masking its existence or the existence of other software."
I have found that ClamAV is not always effective at detecting and eliminating rootkits. Fortunately, the open source Rootkit Hunter is available for download, and it's easy to install. Just use your package manager of choice to install the rkhunter package. There is a man page for rkhunter and you will want to consult it to choose the various options for its use. I chose to take the defaults and just ran it from the command line, 'sudo rkhunter --checkall.' There is a very well written help page provided by the Ubuntu community. Rootkit Hunter is licensed under the GNU Public License, and the source files for Rootkit Hunter are on Sourceforge.
Update: "sudo rkhunter -checkall" changed to "sudo rkhunter --checkall" (added hyphen). Thanks to our readers for the feedback in the comments! -rikki





17 Comments