You may have your DevOps efforts orchestration nailed down, but you should make improving the operational maturity of such implementations an ongoing effort. One tool I use is Red Hat's Ansible, which is fantastic for orchestration and configuration management. The low barrier to entry and simplicity of Ansible are why so many people that start using it learn to love it.
One feature in Ansible that developers should use more often is Ansible Vault.
According to its documentation, the latest iteration of Ansible Vault (1.5) allows for the keeping of "sensitive data such as passwords or keys in encrypted files, rather than as plain text in your playbooks or roles. These vault files can then be distributed or placed in source control."
Often private SSL certificates, API keys, and other sensitive data are released to the public on GitHub or through some other unintended means. Ansible Vault encrypts your secrets via AES256 so that you can safely store them with your Ansible Playbooks and inventory.
Creating a vault file is simple:
ansible-vault create vault.ymlYou will be prompted to enter a password, which you will share with others needing access to the vault. You input your variables, secrets, etc., and save the file when you are done. If you try to edit your vault.yml in a text editor, you will see something like this:
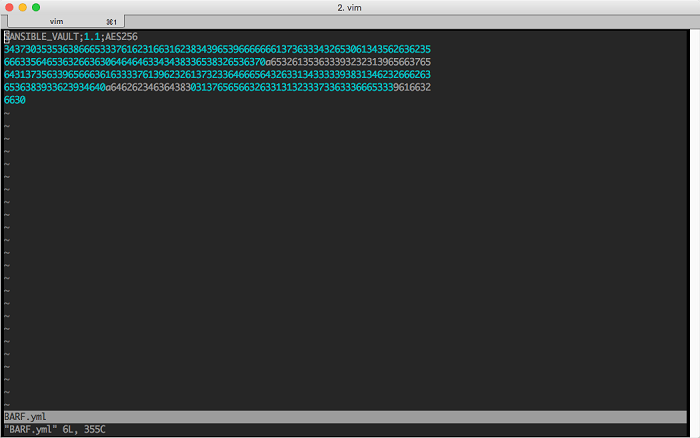
Editing a vault file is as simple as creating one:
ansible-vault edit vault.ymlYou can point Ansible's configuration (ansible.cfg) to a vault-password-file that is outside of your repository. All that goes into this file is your Ansible Vault password. This step eliminates the need for you to type your password every time you edit an Ansible Vault:
vault_password_file = ~/.ansible_vaultIt also allows for a nifty trick when using multiple vault files, such as host_vars and group_vars. If you have a directory that contains your vault files, you can grep all of them for a variable you might have misplaced:
ls -1 | while read N ; do echo -n $N: ; ansible-vault --vault-password-file ~/.ansible_vault view $N | grep STRING ; doneAnother nifty trick is to encrypt SSL/TLS keys with Ansible Vault. This way you can keep them and their configurations in version control. You can encrypt your key(s) with a simple command:
ansible-vault encrypt private.pemThen you can call your key as a variable via a lookup and deploy it to a file on a remote system:
---
- hosts: host.domain.tld
vars:
- private_key: "{{ lookup('file', 'files/private.pem') }}"
tasks:
- name: Place certs on systems
copy: content={{ item.content }} dest=/etc/pki/tls/certs/{{ item.dest }} owner=root group=root mode={{ item.mode }}
with_items:
- { content: "{{ private_key }}", dest: 'private.pem', mode: '0600' }Your decrypted private key will land on the system ready for immediate use.
As you can see, the possibilities with Ansible Vault are endless, and your development and operations can benefit from its use significantly.






1 Comment